From business to everyday users
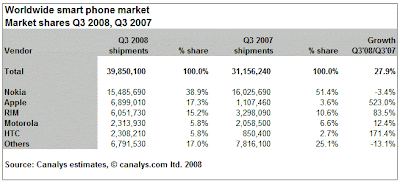
In US, BlackBerry is often referred as CrackBerry, because of its addictive nature. The best way to gauge its popularity is by witnessing most business users checking their emails or sending messages on BlackBerry phones in airports or even in business meetings. Smartphone has been the weapon of choice for business users, who use it everyday including weekends to find contact information, check schedule, and read and send emails. Those functions were essential to conduct business on-the-go and enough to pay premium for the phone and the service. In addition, since most businesses use Microsoft Exchange for contact management, calendar and email, most smartphone vendors support integration with Microsoft Exchange. While Nokia has the highest market share (~39%) in worldwide smartphone market, US market is dominated by RIM (Research-In-Motion, manufacturer of BlackBerry phones) with about 40% market share followed by not so surprisingly Apple with about 30% market share. Market shares of Microsoft and Palm smartphones have been falling since early 2006, and the same trend continues.
Thanks to Apple’s iPhone, now the flood gate has opened. Prior to iPhone, a slick, trendy version of BlackBerry called Pearl and low-price PDA-type phones called Palm Centro had gained some popularity among non-business users. Introduction of slew of Google mobile applications – Gmail, Google Maps, Calendar, Google Search, and YouTube to name a few – also helped more and more everyday users to appreciate smartphones. Another catalyst was carrier’s introduction of unlimited data plan. But the real tsunami began with Apple iPhone. According to comScore’s report in October 2008, adoption of iPhone by low-income demographics increased 48% from June to August 2008. Interestingly enough, iPhone was a smartphone targeted for consumers, but with Microsoft Exchange integration support, more and more business users are adopting iPhone as welll. The following numbers regarding iPhone are quite staggering, considering that iPhone was introduced to the market only about one year ago.
- Best selling phone (6.89 million phones) in the US during Q3 2008 – not just in smartphone category. (Source: The NPD Group)
- Ranked number two in worldwide smartphone market with 17.3% market share and 523% Year-over-Year growth according to a report by Canalys.
- 300 million apps downloaded through App Store. (Source: Apple)
- Average of 2.2 million apps downloaded per day. (Source: Apple)
- More than 10,000 apps have been uploaded to App Store. (Source: Apple)
Another new entrant to the smartphone market with much anticipation was Google’s Android-based G1 smartphone. These two phones, iPhones and Android-based phones will be the center of smartphone revolution now and in the near future.
Openness wins, again
The major reason for explosive growth of iPhone could be attributed to the App Store. Yes, it looks good and multi-touch screen is revolutionizing the whole intuitive user interface movement, but the real drive is its openness. Before iPhone, most phones manufacturers guarded their phones like a walled garden. It has happened over and over before, where too many restrictions hindered true innovations. Users received whatever phone manufacturers or carriers decided to allow. But, iPhone provided a platform for developers to offer their software – for a profit if they wish – and more importantly gave users choices. Users decide what they want to download and/or buy. Developers have motivation to write good programs, better than other developer, so that their software could be purchased more and thus make more money. It’s truly a beautiful system and ingenious business model. The numbers I described above are clear evidence. If the rumor that Apple may introduce $99 version of iPhones before Christmas is true, it would be truly game-changing plan.
The whole premise behind Google’s Android-base G1 phone was also the openness. It’s even more open than iPhone since its operating system (Android) is open source and it does not have as stringent software review process as Apple. Starting December 5, Google is offering a development version of the G1 phone that is both SIM and hardware unlocked. It only costs $25 registration fee to register as a developer on Android Market, and pay $399 for the hardware. Google also plans to expand the territories that it’s available in, but initially it can be purchased in the US, UK, Germany, Japan, India, Canada, France, Taiwan, Spain, Australia, Singapore, Switzerland, Netherlands, Austria, Sweden, Finland, Poland, and Hungary. It’s a shame that most mobile-phone advanced country like Korea is not on the list. Korean mobile phone manufacturer had better wake up to the new mobile world, otherwise they may end up losing a lot of their market shares.
These two phones are shifting entire paradigm in not just smartphone market, but overall mobile phone market. As “Internet” generation grows up and adopt mobile behavior similar to that of desktop and Internet, demand for “open” mobile phones will grow stronger and stronger. It would not be too surprising that most of mobile phones in the future will follow Apple and Google’s model.
Open with care
Today’s smartphones do not deserve to be called phones. They are small computers and mobile phone capability. iPhone’s specification is better than even Playstation Portable (PSP).
And this is only the beginning. Be it mobile WiMAX or LTE, carriers will keep upgrading their networks to meet the demand and support faster bandwidth. Apple, other manufacturers of Android-based phone and incumbents will continue to push the envelope, developing better, faster, lighter and more powerful mobile devices. Does this sound familiar? Continuous improvement is no stranger to high tech world, but specifically it parallels laptops. When laptops first came out, they were much inferior to the desktops, as desktop PCs were to mini-computers much earlier. Nowadays, most laptops have become as powerful as desktops. And the day smartphones will be as powerful as laptops is just around the corner. They are not going to replace them, as we still have mainframes, mini-computers, desktops and laptops. They will all co-exist and serve specific roles.
The Internet opened the door to the world, where one can reach anywhere for instant access to any information he or she desires. Also, we have seen some who try to take advantage of the openness. In the dawn of desktops, malware then was limited to virus, and it had very limited way to distribute itself. With open network, where you can reach anyone, anyone can reach back to you. It doesn’t help to have vulnerable operating system and communication tools in the most desktops. Also, as opposed to hobby-like nature of virus writing in the beginning, financial gain is the main purpose of today’s perpetrators, and motivation to write good (?) and tenacious malware is much higher. Open network/system and free market are encouraging creative innovations not only in productivity but also in cybercrimes.
Mobile world is the next frontier (for cybercriminals)
There is a new report just published by Information Security Center of Georgia Tech, which predicts that mobile phones will be next target for botnets. It’s inevitable, as mobile phones are getting more powerful, faster Internet connection is possible and thus user behavior on mobile phone is shifting from voice communications to online communications. Previously, carriers charged users by number of SMS messages or amount of data used, but nowadays most carriers offer unlimited SMS and data plan at very attractive pricing points. The new rate plan in addition to the fact that mobile phones tend to be always on and often security is poor will make them even more attractive target for cybercriminals. The shifting user behavior makes similar “drive-by download” in mobile phones as in desktop possible. Also, another large difference between desktops and mobile phones is the sheer volume. There are estimated to be around three (3) billion mobile phones used worldwide, as opposed to about 800 million desktops. Apple and Google review the uploaded applications before publishing them to the public, but there is no guarantee that they will catch all of the malware.
With relatively low bandwidth, it’s hard to imagine mobile botnets launching massive DDoS (distributed denial of service) attacks. At least not the bandwidth flooding attacks, but logical and protocol attacks are certainly possible since there are so many more mobile phones available than desktops. For example, SYN flooding is quite possible with mobile phones, since it works by sending many requests to a sever and depleting its “half-open” session table, which is able to handle only about 1024 entries. More than DDoS attacks, there is more possibility of fraud and privacy invasion. Malware on the mobile phone can access paid contents and charge to user’s mobile phone account. Since mobile phone stores phone numbers of owner’s contacts, SMS spamming or even personal data leaking is possible. In places like US and others where there is tighter integration between mobile phones and company’s internal resources, the possible damage of data leak is even greater. Also, since user’s location can be pin-pointed using GPS data, a cybercriminal can track certain users for stalking or other criminal purpose. I know certain some companies in Korea already do this, so it shouldn’t be completely inconceivable. There is already an application like FlexiSPY that is used to spy on user activity. After FlexiSPY is installed on a smartphone, it allows you to use the phone to read SMS, e-mail, and call logs from the smart phone from anywhere in the world. The Windows Mobile and Symbian versions even allow you to listen to actual phone calls being made with the smartphone and use the phone as a secret GPS tracker.
There is also no doubt that some cybercriminals will use these powerful smartphones as a tool to a cybercrime.
Seize the opportunity
So far, any serious, widespread malware has been unheard of. It’s because until just about a year ago before iPhone and Google’s Android phones, most phones operated in closed, walled-garden environment. But, as amazing success of iPhone shows, there is huge paradigm shift happening in the mobile phone market right now. I have mentioned several ways cybercriminals can benefit from compromised mobile phones, but if I can think of them, cybercriminals may already have thought of many more creative ways. It’s only a matter of time. There is a great opportunity for a security company to dominate mobile security market. There are already many anti-virus and SMS anti-spam programs are available for all popular mobile operating systems from companies like AirScanner, F-Secure Corp., McAfee Inc., Symantec Corp., SMobile Systems, Trend Micro Inc., and Sophos plc., but none of them is a clear leader yet. Many IT departments in US already have or are in the process of creating mobile security policy. Just as in desktops, they will require installation of security software (anti-virus, firewall, and/or encryption) on smartphnes and can restrict which software can be installed. So far, no major mobile security threats have been widely reported, so they are not on consumers’ radar yet. But, it will just take one outbreak for them to come to the realization. In addition to security software on smartphones, carriers or other 3rd-party vendor could also provide network-based, cloud security services by scanning all mobile data on network level.
For consumers and non-business users, they need to employ the same cautious behavior as in desktop environment. They should always be careful when downloading an application or clicking on a link. Just as in desktop, even with whatever mobile security software they have on the phone, they will not be able to catch everything. They should also create password to access the phones so that their information is relatively safe when stolen. But as in desktop, most users may choose convenience over security, which would be a great tragedy since they may become the source of a large outbreak.
In conclusion, it should come as no surprise that technology advance always comes with double-edged blade. While open smartphones promise another whole new level of productivity gain (or loss to some), they come with a quite strong warning label. But those who seize opportunity will reap great benefits.